The Beyond Blog
.png)
15 Sep 2025
Universal Identity Defense for Legacy and On-Prem Applications with Beyond Identity and CrowdStrike
Extend phishing-resistant MFA to Kerberos, NTLM, LDAP, SMB with Beyond Identity + CrowdStrike.

30 Aug 2023
August 30, 2023
What's the Difference Between Passkeys and Passwords?
As a developer, you understand the importance of ensuring the confidentiality and integrity of digital interactions.

30 Aug 2023
August 30, 2023
Are Passkeys 2FA?
While the increasing adoption of passkeys is exciting, many developers are left wondering about the technical and security nuances.

29 Aug 2023
August 29, 2023
Why Companies Need Both Zero Trust Authentication and Identity and Access Management
Using Zero Trust Authentication and an IAM solution are one of the best ways to reduce a company’s cybersecurity risk and overall impact of a cyber threat.

16 Aug 2023
August 16, 2023
Introducing The Passkey Journey: Free Tool to Simplify Passkey Adoption
While passkeys represent a significant step forward towards greater safety, privacy, and accessibility on the internet, deployment remains challenging for development teams.

16 Aug 2023
August 16, 2023
Introducing The Passkey Journey: Free Tool to Simplify Passkey Adoption
Beyond Identity launches free development tool to help teams integrate passkeys into their applications quickly and confidently

07 Aug 2023
August 7, 2023
Security Deep Dive: Hardware-Bound Versus Software-Bound Passkey
Passkeys are seeing rapid adoption. However, where passkeys are generated and stored has an impact on security.
28 Jul 2023
July 28, 2023
July Hacker Tracker
Welcome to the July 2023 Hacker Tracker, where we’ll provide a breakdown of the most high-profile cyberattacks in the past month.
25 Jul 2023
July 25, 2023
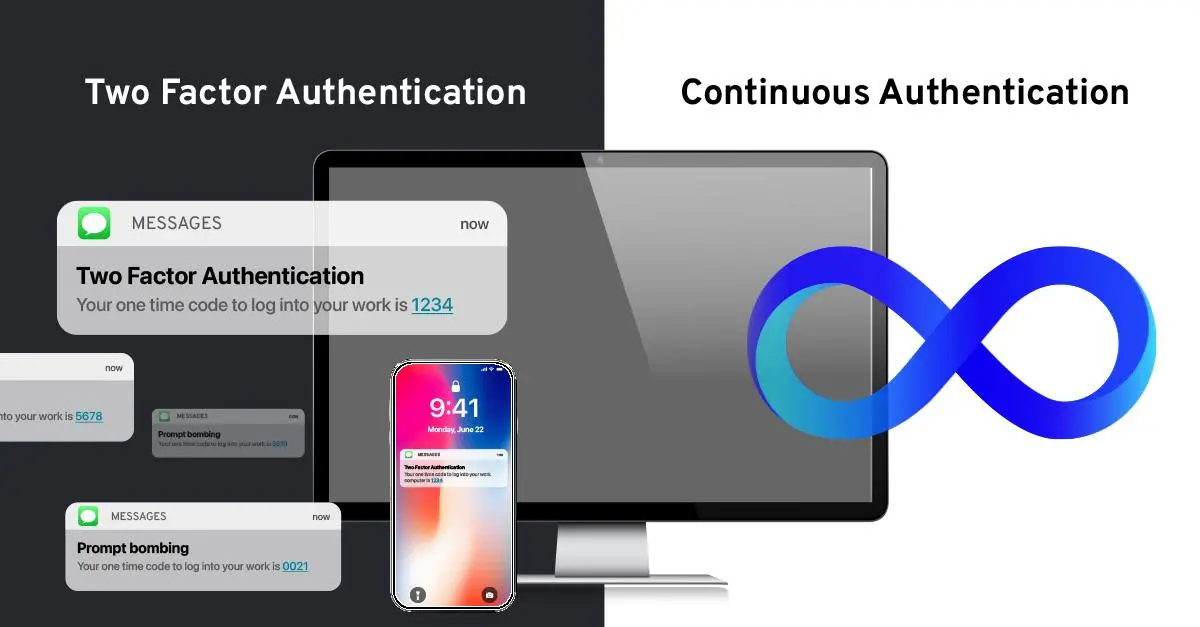
How is Continuous Authentication Different from Two-Factor Authentication?
Traditional MFA is falling short due to the static, one-time verification. Continuous authentication makes security dynamic and robust.

19 Jul 2023
July 19, 2023
California Cell Phone Reimbursement Law: Stop Two-Device MFA Costs
Employees are likely using personal resources for work. California law states that employers must reimburse a reasonable portion of these costs.

