Resource Library
Explore our collection of resources covering the latest in cybersecurity, industry trends, and expert insights
_1.avif)
16 Mar 2021
March 16, 2021
451 Business Impact Brief
Overcoming the Hassle of Passwords and MFA with Passwordless Authentication.
05 Mar 2021
March 5, 2021
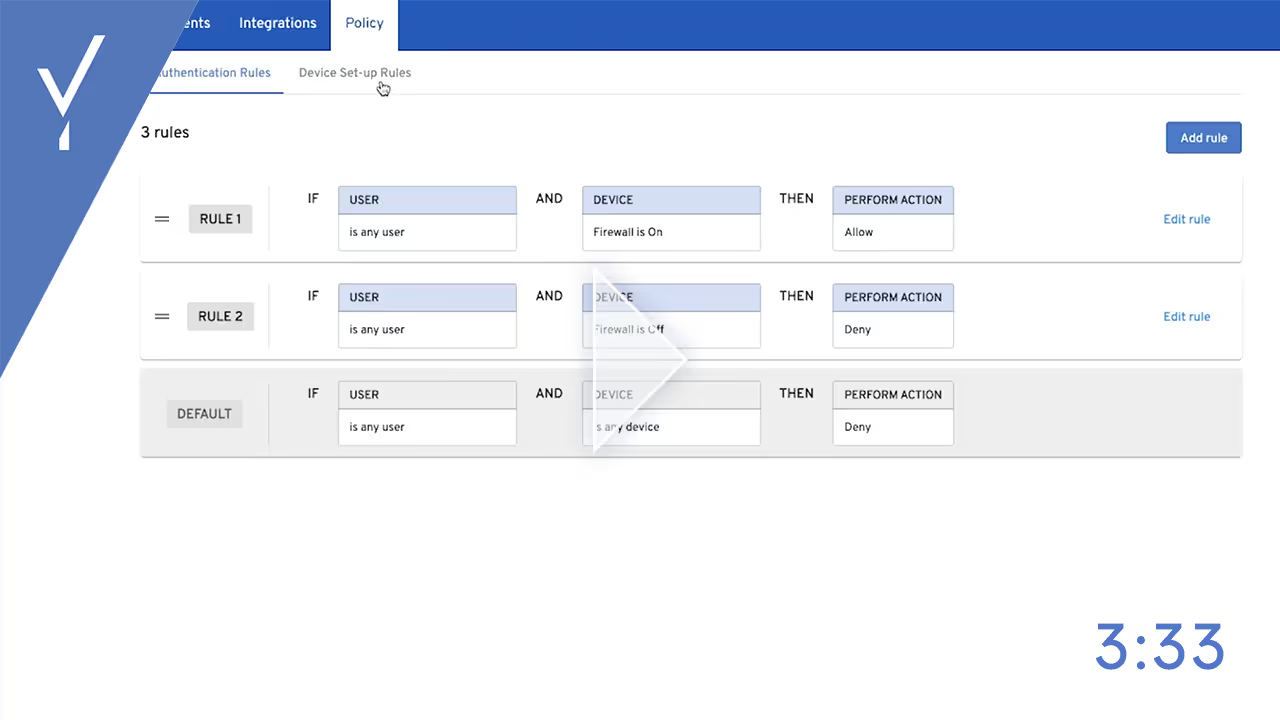
Risk Policies and Step-Up Authentication
Learn how to create risk-based access policies in the Beyond Identity Console.
05 Mar 2021
March 5, 2021
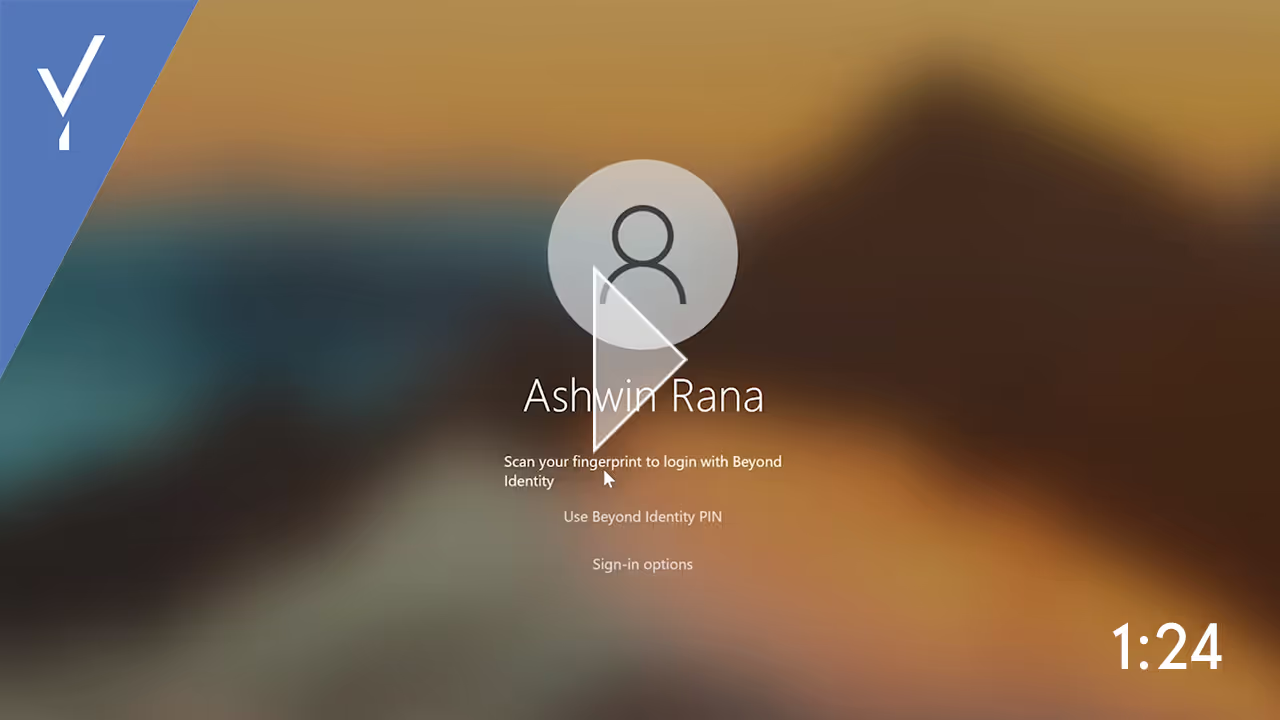
Passwordless Desktop Login
Take a look at the user experience for the passwordless desktop login. This desktop login is available for both Windows 10 PCs and Macs. Users can authenticate into their domain-joined desktop using either their fingerprint or PIN.
05 Mar 2021
March 5, 2021
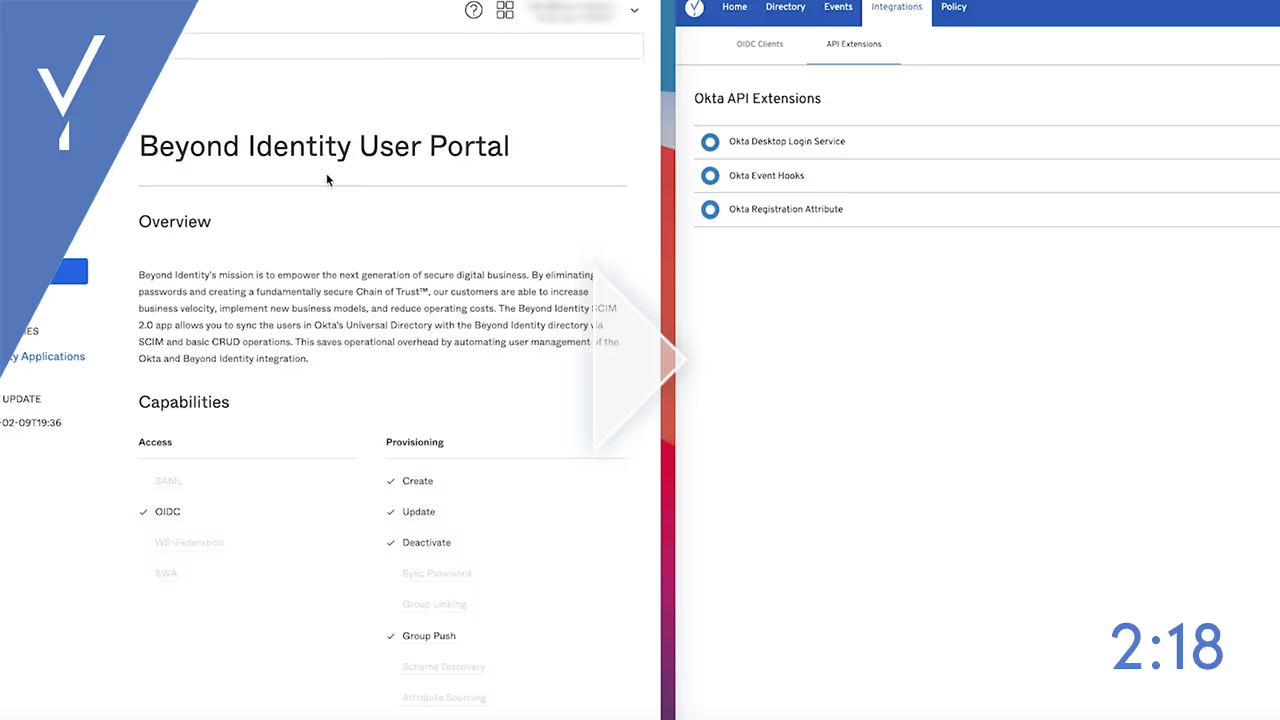
Integrate Beyond Identity with Okta
Discover how to integrate Beyond Identity into your Okta single sign-on.
05 Mar 2021
March 5, 2021
Beyond Identity Admin Console Overview
Explore administration in the Beyond Identity Console.

24 Jan 2021
January 24, 2021
What is asymmetric cryptography and how does Beyond Identity use it?
Jasson Casey, CTO of Beyond Identity, discusses the difference between symmetric and asymmetric secrets and how these cryptographic principles are used by Beyond Identity to eliminate passwords completely.
24 Jan 2021
January 24, 2021
Passwordless SSO Login
Take a look at the user experience for the passwordless login to single sign-on applications through Beyond Identity.

24 Jan 2021
January 24, 2021
Mario Duarte, VP of Security at Snowflake, on going beyond passwordless with Beyond Identity
Mario Duarte, VP of Security at Snowflake, discusses how Beyond Identity not only helps Snowflake be more secure, but also helps their employees.

