Resource Library
Explore our collection of resources covering the latest in cybersecurity, industry trends, and expert insights

28 Jun 2023
June 28, 2023
Device Trust: A Key Element of Zero Trust Authentication
Zero Trust Authentication helps you continuously ensure that only authorized users can connect to your network—and only access the resources needed.
27 Jun 2023
June 27, 2023
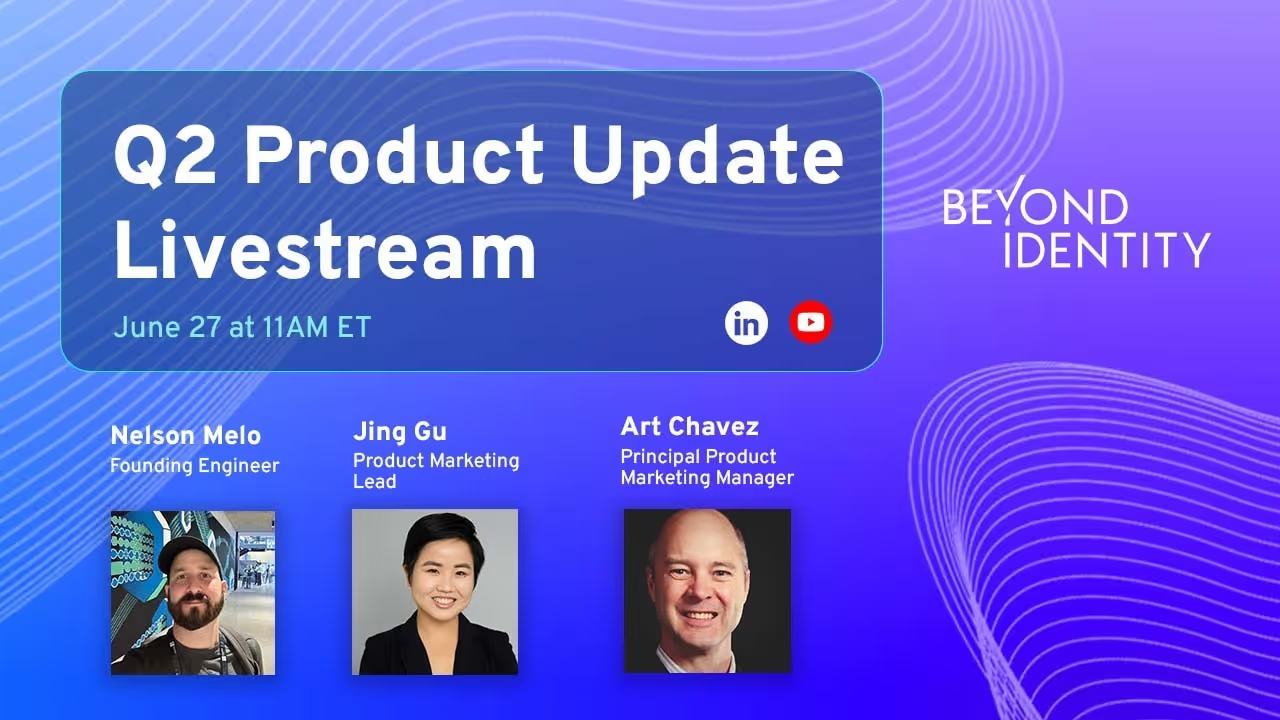
Q2 Product Update Livestream
Receive the latest insights on Beyond Identity's new product features, enhancements, and upcoming releases.

08 Jun 2023
June 8, 2023
The Future of Hacking is AI
AI technologies like ChatGPT may make it easier for cybercriminals to steal sensitive data. To measure the threat, we tested ChatGPT's hacking ability.

08 Jun 2023
June 8, 2023
Browsing in the Age of Malware: the Most Dangerous Work-Related Search Terms
Discover the most dangerous work-related search terms, and take proactive steps to safeguard your device against malware while working or job searching.

05 Jun 2023
June 5, 2023
Zero Trust: Sentiments of Cyber Security Professionals
We've targeted cybersecurity professionals to gauge their expertise on zero trust-its value, challenges, costs, and future.

01 Jun 2023
June 1, 2023
Zero Trust Means Attackers Shouldn't Trust You
On this episode of the Cybersecurity Hot Takes podcast we are joined by CISO, Sam Curry from Zscaler.
09 May 2023
May 9, 2023
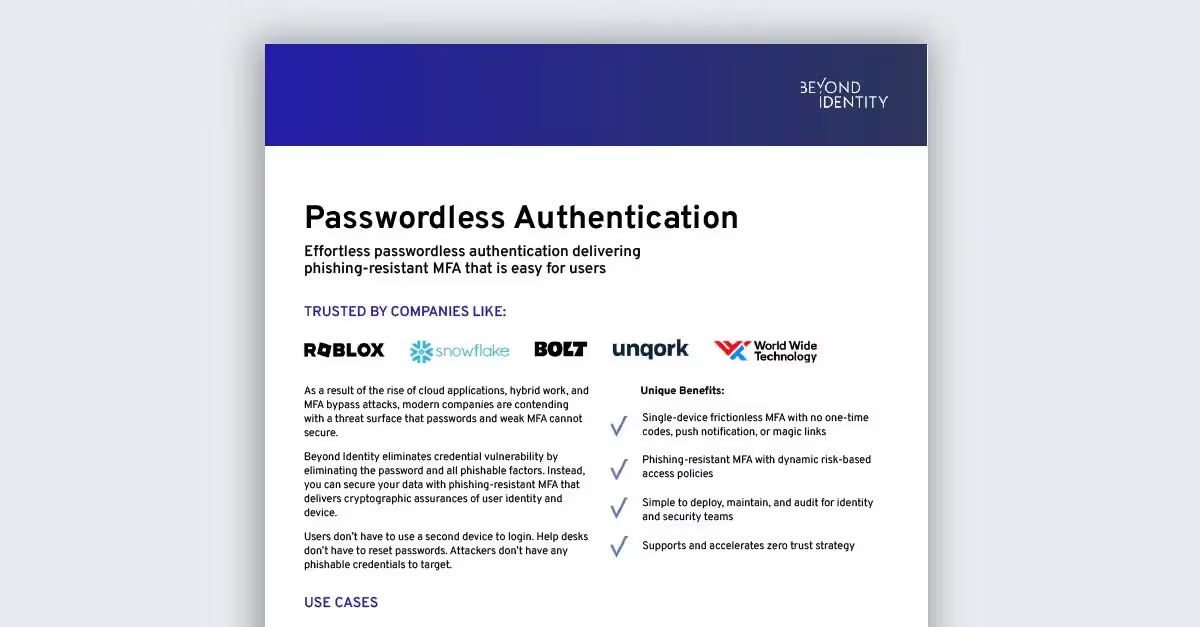
Passwordless Authentication
Secure your data with phishing-resistant MFA that delivers cryptographic assurances of user identity and device.

05 May 2023
May 5, 2023
Zero Trust Authentication that Fortifies IT and Inspires Users
Jasson Casey, Chief Technology Officer at Beyond Identity, discusses zero trust architecture and the future of Beyond Identity.

