Unified Identity Security
IAM, reinvented
for security
The only IAM platform that eliminates identity-based attacks with continuous, phishing-resistant access control.
- Eliminate your #1 threat vector: the credential
- Secure critical apps with continuous user and device verification
- Meet Phishing-Resistant MFA mandates from day one

- Protect access from managed and unmanaged devices
- Gain deep device posture visibility across your fleet
- Block access if your EDR, MDM, and ZTNA flags a risk

- Remove phishable credentials and block access from non-compliant devices
- Define precise, app-by-app access controls
- Aligns with Zero Trust and phishing-resistant mandates

- Verify both the user and the device behind the camera or chat
- Guarantee user and device authenticity, without “deepfake detection”
- Gain tamper-proof visual assurance of participant authenticity





no shared secrets
Always phishing resistant
Device-bound passkeys replace passwords, OTPs, and second-device factors like push notifications that attackers easily bypass.
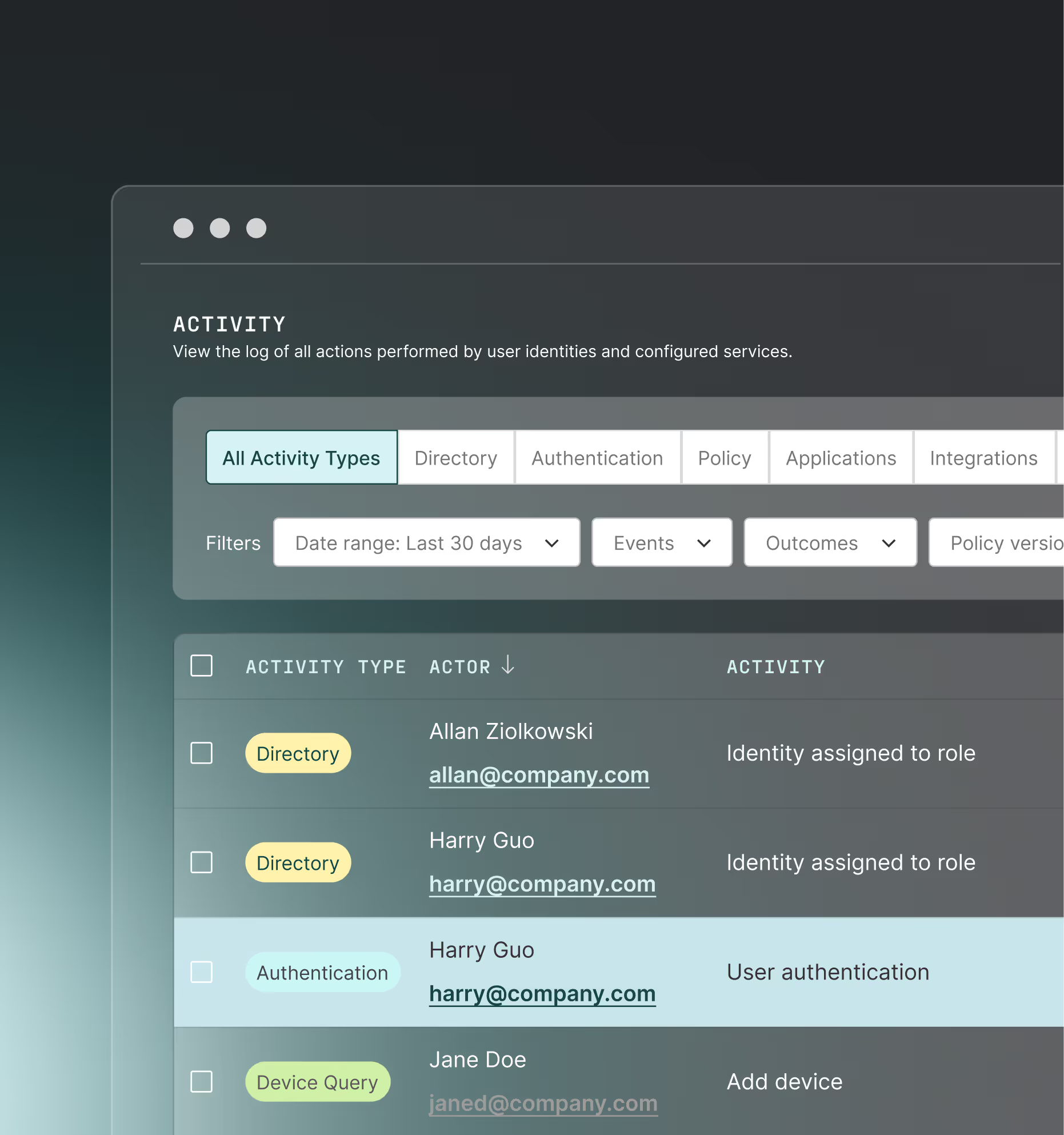
continuous risk signals
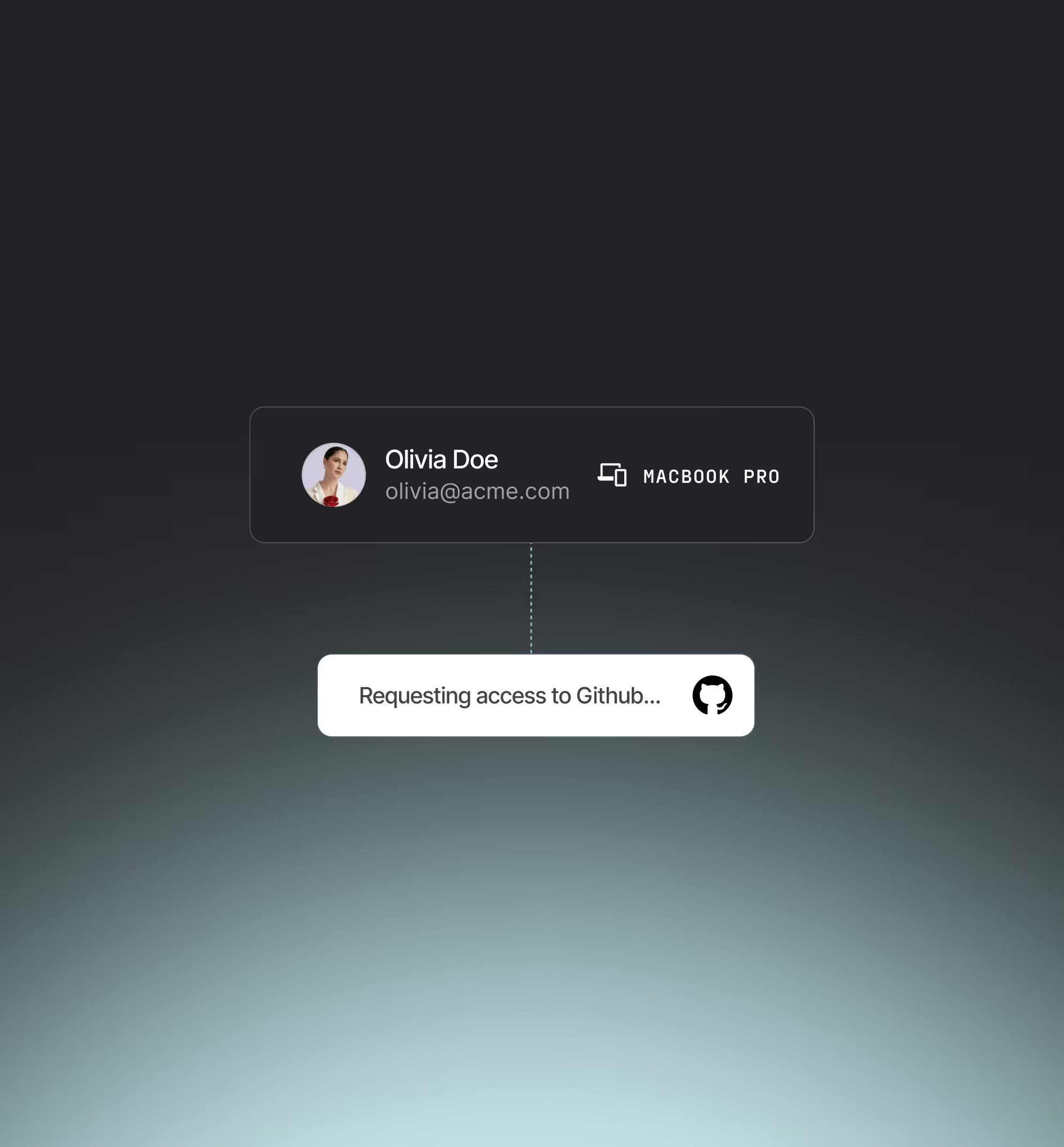
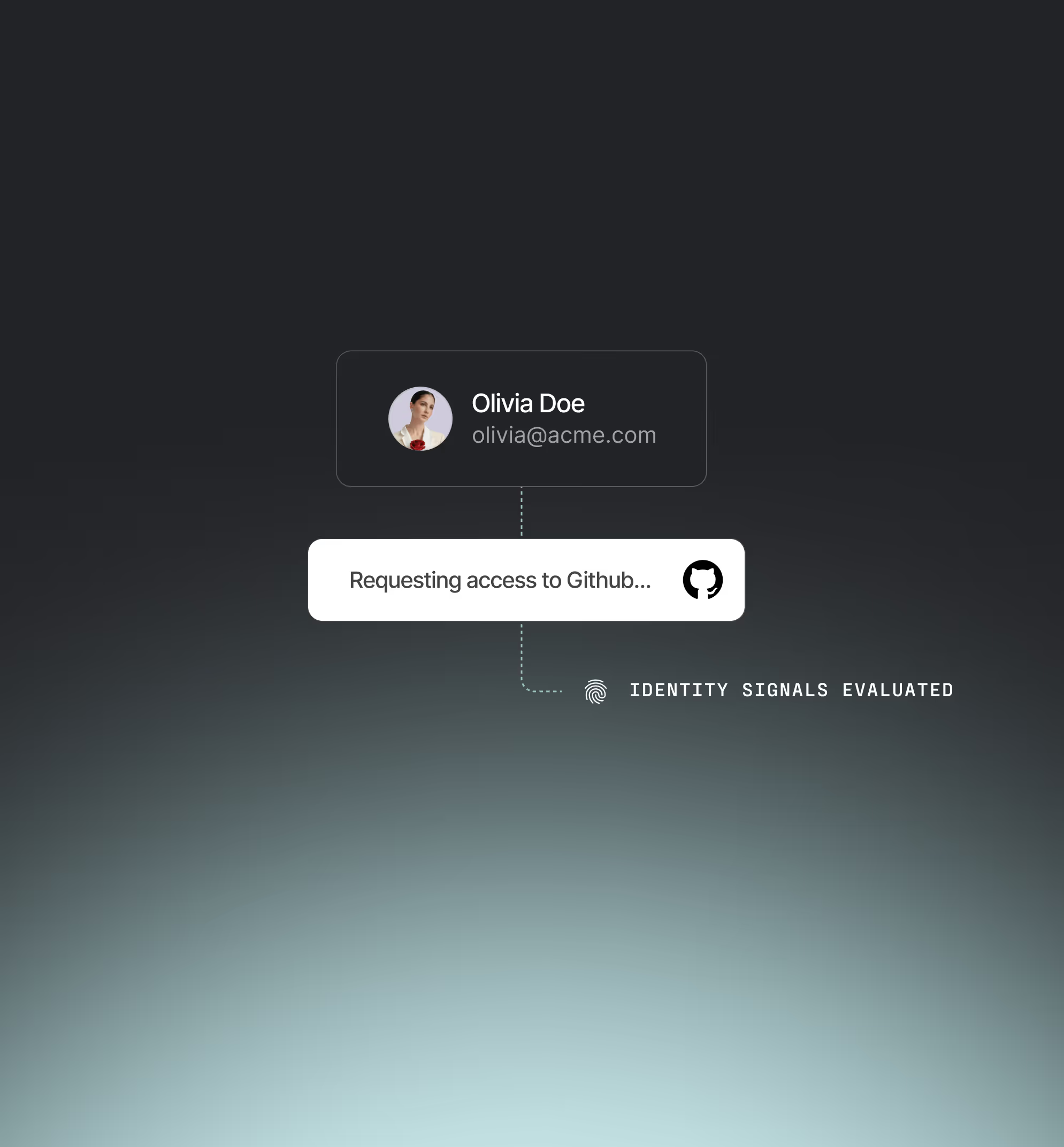
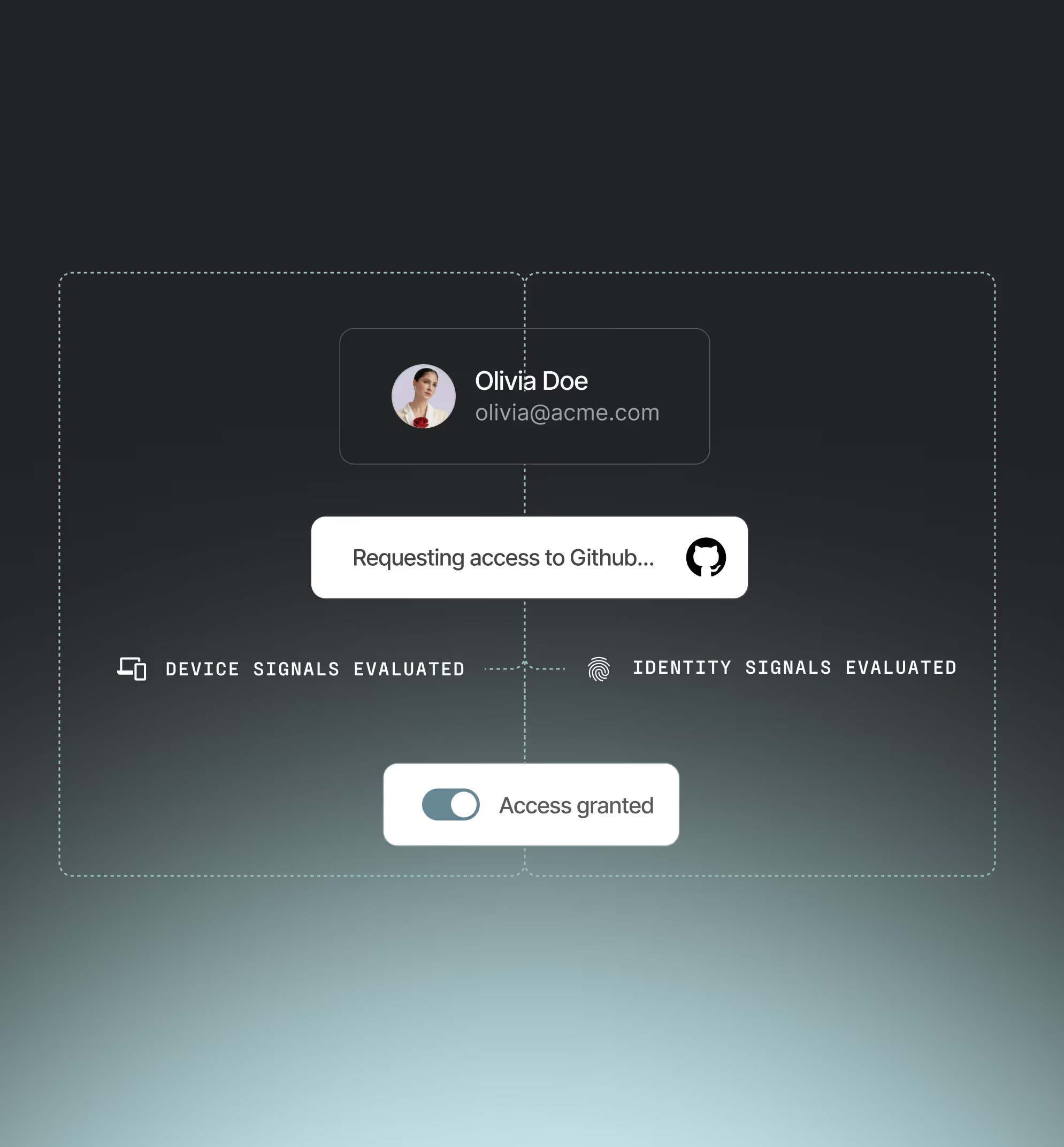
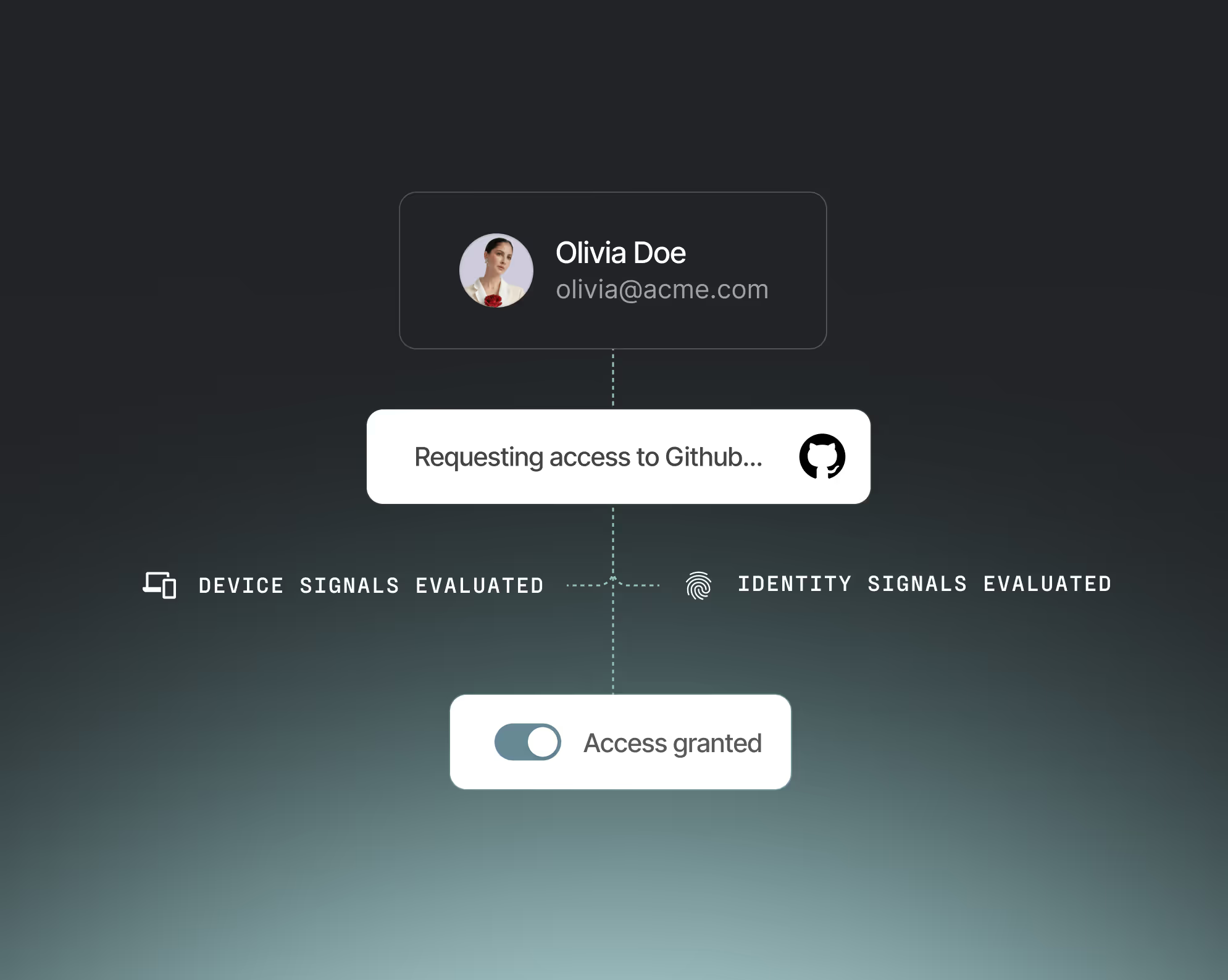
Continuous risk-based authentication
Monitor real-time risk from identity, device, and behavioral signals — no stale session assumptions.
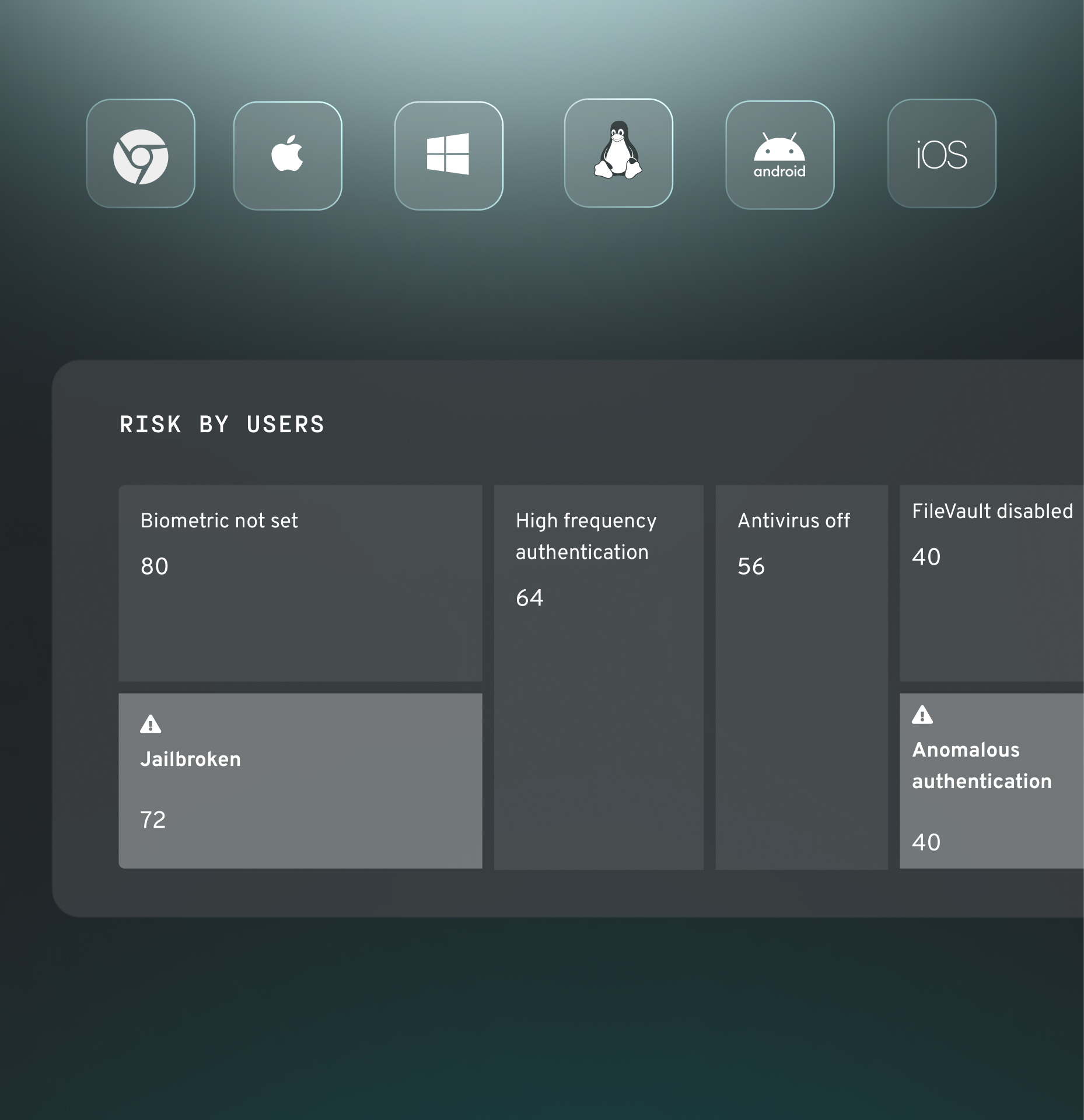
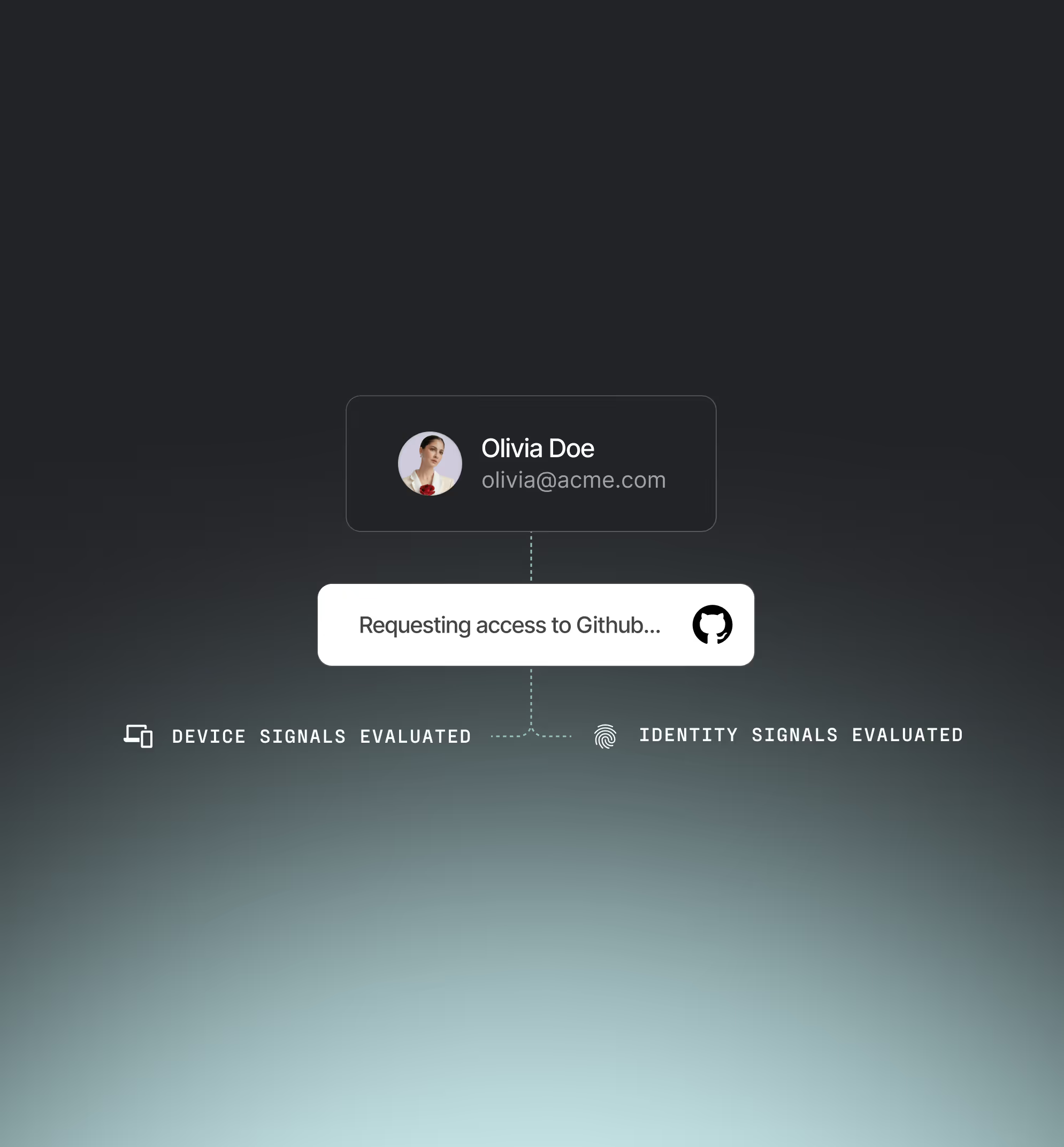
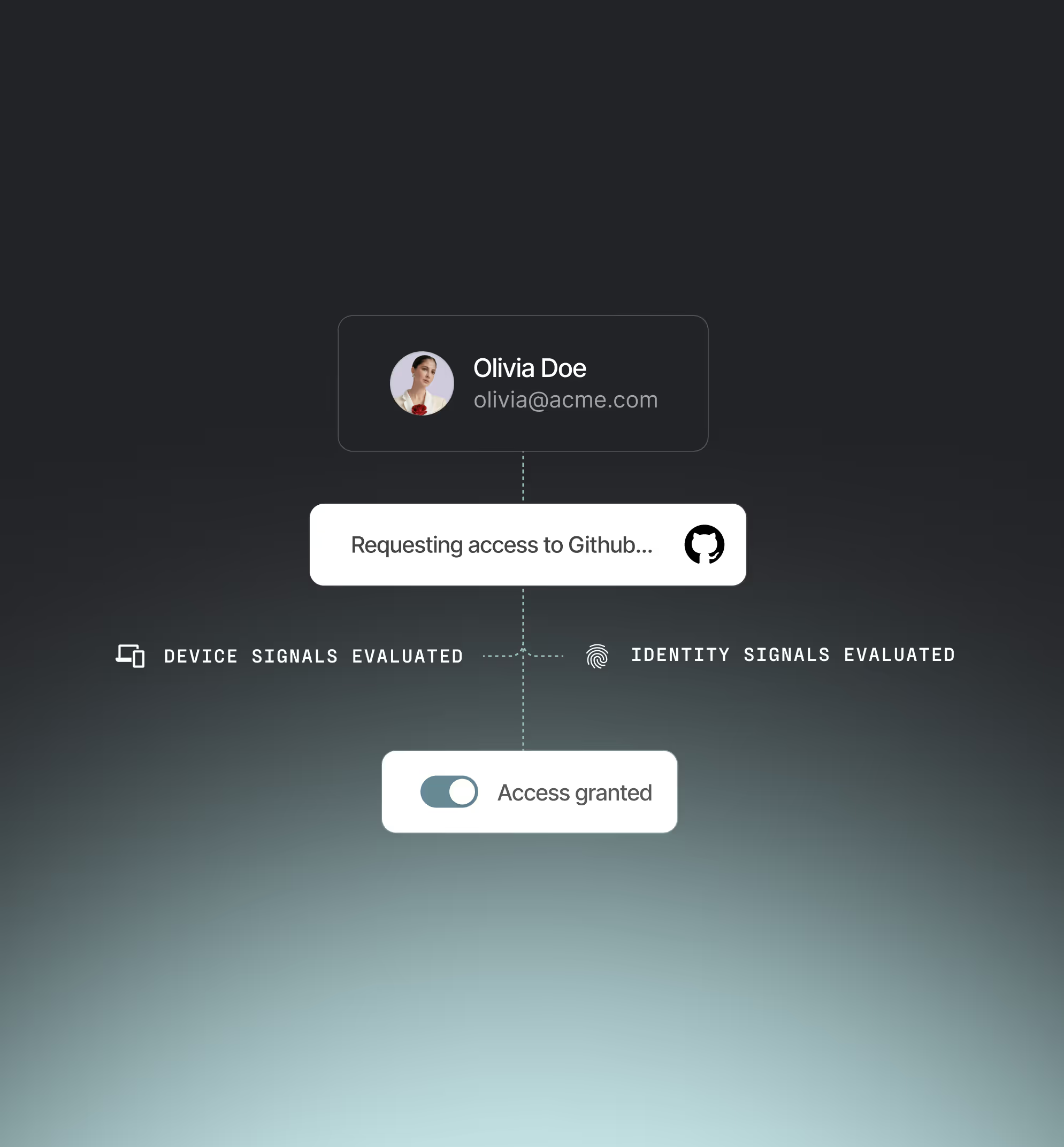
Device trust
Device security compliance
Enforce posture-based policies across all devices, whether managed, BYOD, or contractor-owned.
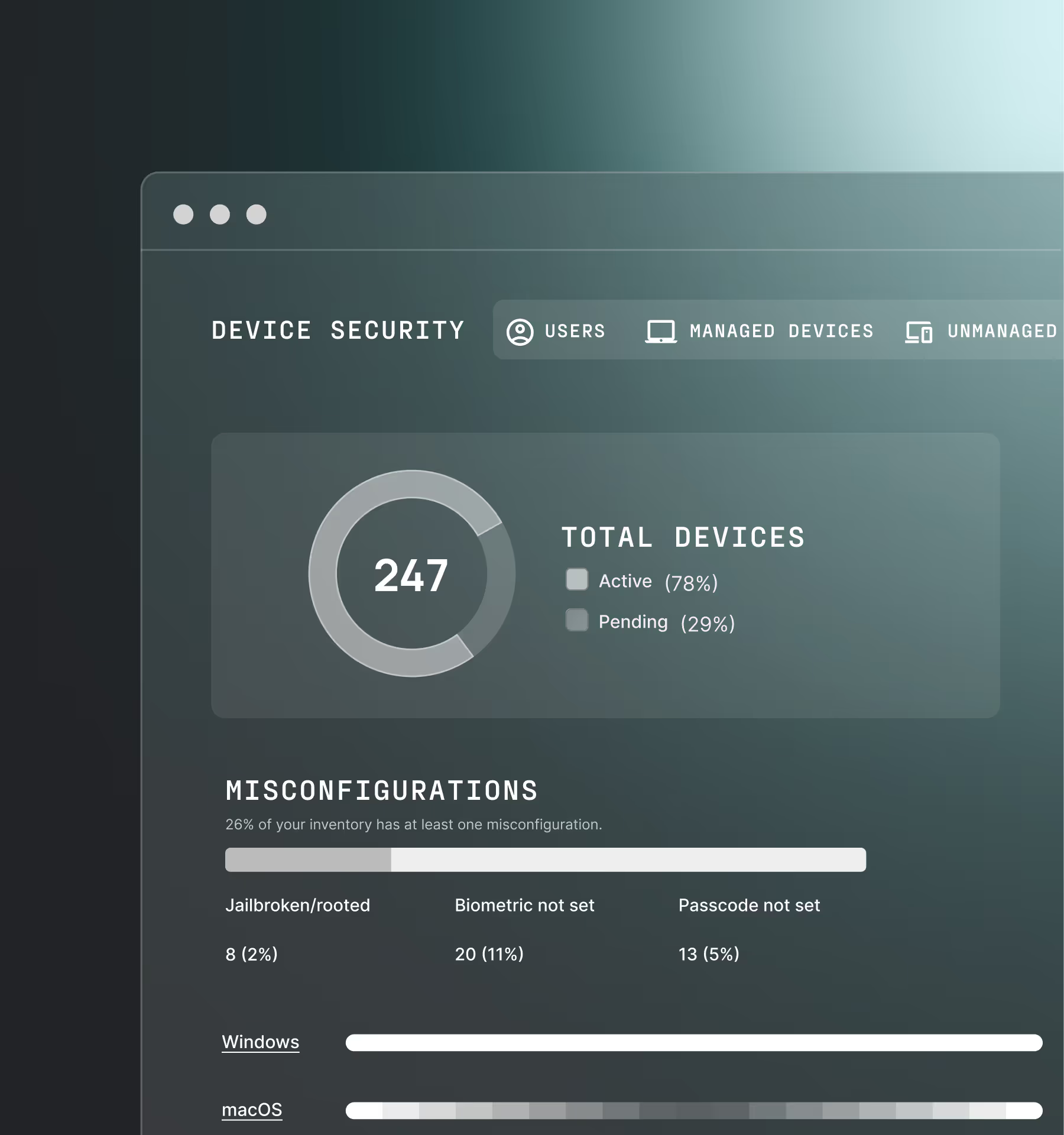
Customizable policies
Customizable access control
Easily configure customizable, adaptive risk-based policies tailored to your exact security and compliance requirements. Leverage signals natively collected by Beyond Identity and other security tools in your stack.
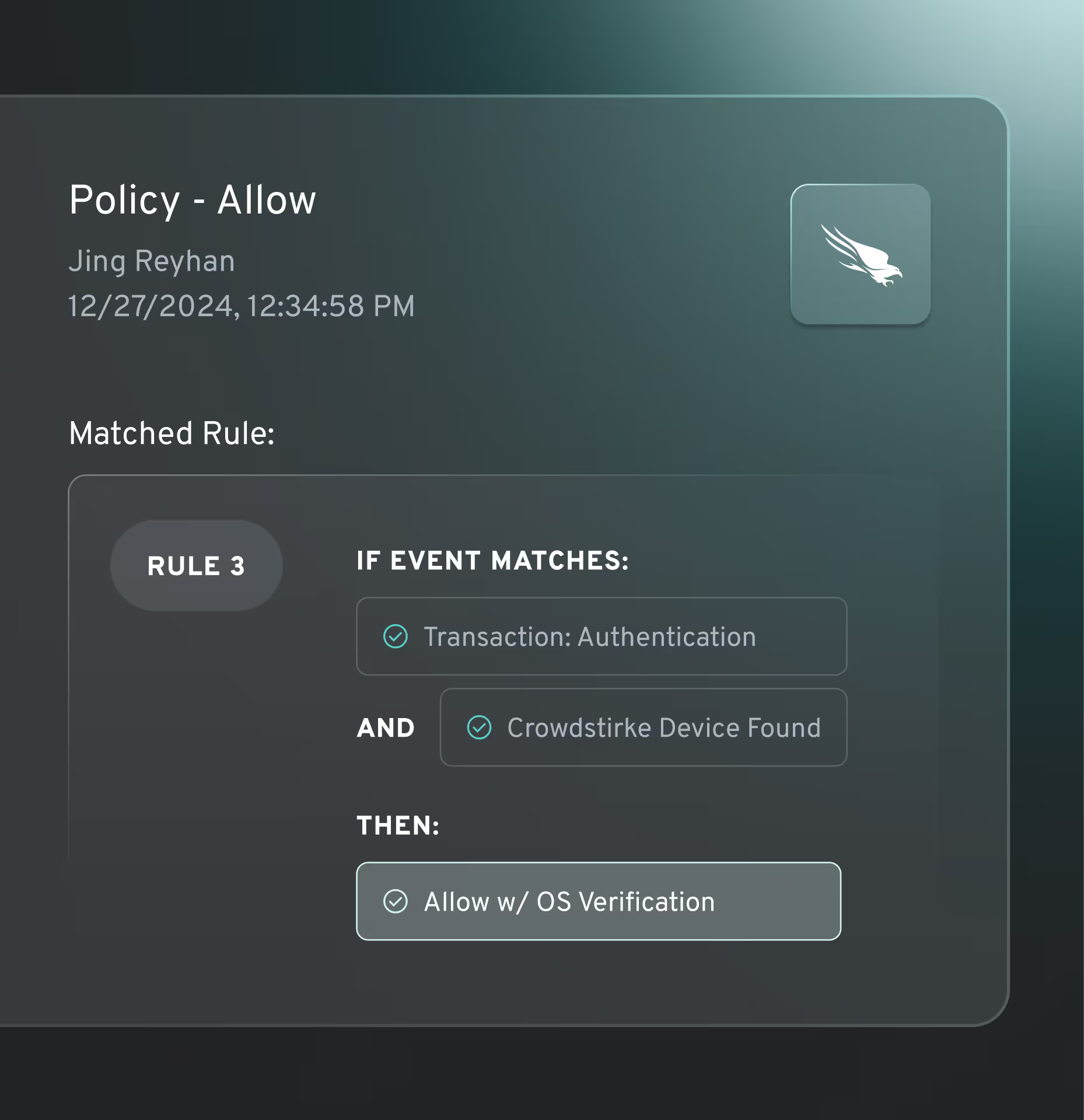
complete OS operability
Universal OS support
Protect every user and device across Windows, macOS, iOS, Android, Linux, and ChromeOS.
.jpg)



.avif)

.avif)
.avif)
.avif)


.avif)

.avif)



.avif)

.avif)


