The Beyond Blog

22 Jan 2026
Beyond Identity Opens Early Access for the AI Security Suite
Gain visibility and control over autonomous AI agents with Beyond Identity's AI Security Suite. Enforce identity, device context, and data governance with cryptographic proof. Early access is now open!
22 Apr 2021
April 22, 2021
Is Two-Factor Authentication (2FA) Worth It?
There are many ways in which 2FA can be breached, hacked, or manipulated, resulting in huge problems for your organization.

12 Apr 2021
April 12, 2021
Announcing Beyond Identity’s New Auth0 Integration
Beyond Identity integrates with Auth0 to provide customers with strong security without compromising the user experience.
06 Apr 2021
April 6, 2021
How to Ensure Security Settings Are Configured Properly on Your Employees' Devices
Now there’s a way to gather security context from managed and unmanaged devices in a single solution so you can make secure access decisions.

05 Apr 2021
April 5, 2021
Introducing New Device Context and MDM Integrations
There’s now 25+ new attributes to use in risk policies, plus new integrations with the most popular MDMs: Jamf, Microsoft Intune, and VMware Workspace ONE UEM.

29 Mar 2021
March 29, 2021
Can Passwordless Authentication Replace My MFA?
What’s next for those who are in search of the holy grail of fundamentally secure authentication? It starts with eliminating passwords, completely.
23 Mar 2021
March 23, 2021
How to Prevent Phishing: A New Approach
Protection against phishing has failed, leaving our passwords and psyches vulnerable. What if there were a more straightforward solution?
11 Feb 2021
February 11, 2021
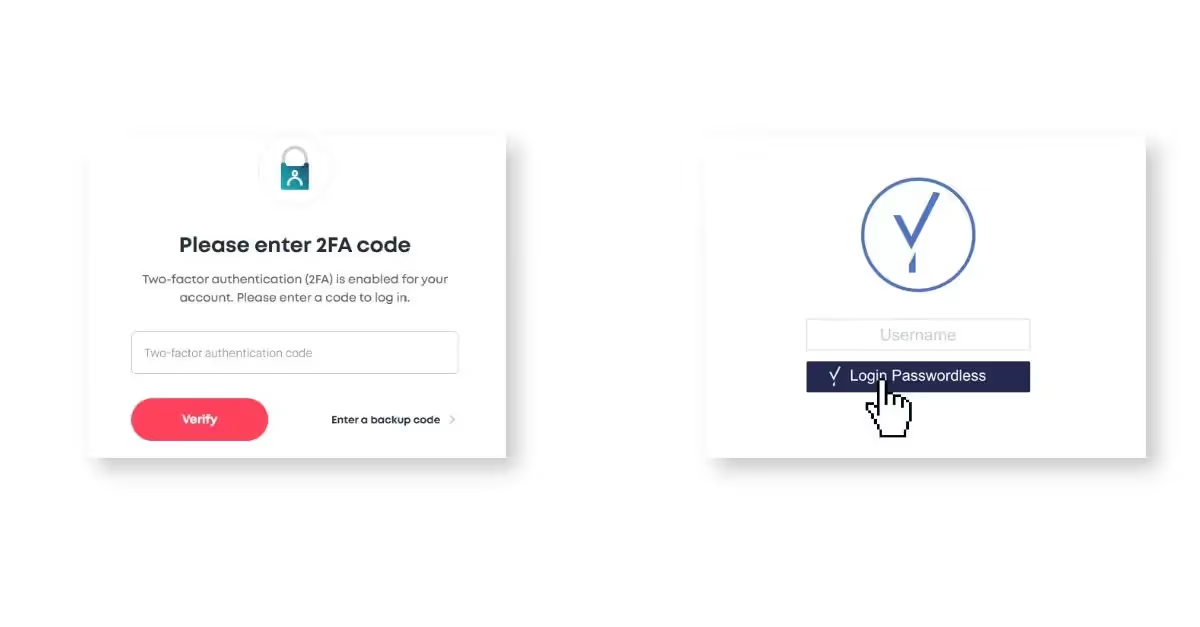
Traditional Two-Factor Authentication vs. Beyond Identity’s Passwordless Authentication
Traditional MFA remains the default for dealing with insecure authentication. We hope to interrupt the “passwords are bad, so we need MFA” refrain.

11 Feb 2021
February 11, 2021
Is it finally time to kill traditional Two-Factor Authentication and Multi-Factor Authentication?
The traditional two-factor or multi-factor authentication solutions that companies are currently using can and should be replaced by something that is far more secure and much easier to use.

12 Jan 2021
January 12, 2021
Here Are Some of the Ways They Stole Passwords in 2020
Here we’ll present the notable methods – some old, and some new – that hackers used to steal passwords in 2020.

