The Beyond Blog
.png)
15 Sep 2025
Universal Identity Defense for Legacy and On-Prem Applications with Beyond Identity and CrowdStrike
Extend phishing-resistant MFA to Kerberos, NTLM, LDAP, SMB with Beyond Identity + CrowdStrike.
15 Jul 2021
July 15, 2021
What Is The TPM (Trusted Platform Module) And Why Is It Important?
If you’re working from a modern computer, chances are there’s a TPM inside. Learn more about the trusted platform modules and what it is designed to do.
13 Jul 2021
July 13, 2021
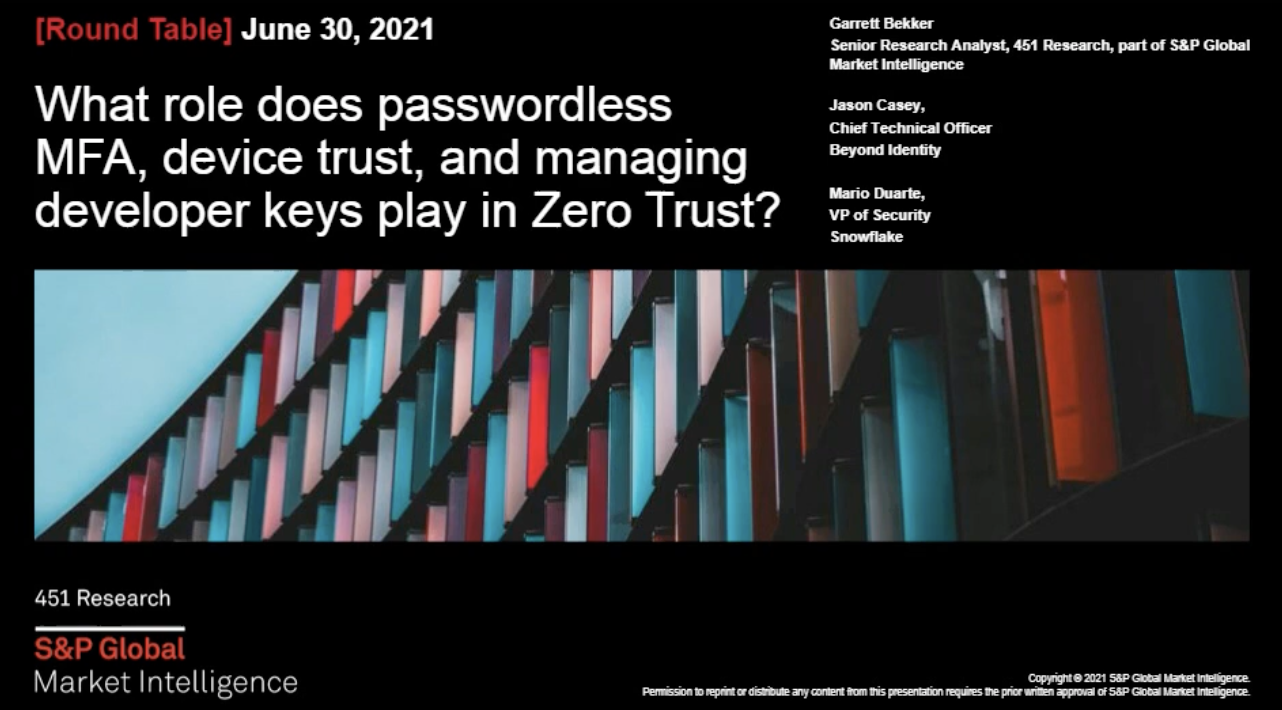
451 Round Table Recap
What Role Does Passwordless MFA, Device Trust, and Managing Developer Keys Play in Zero Trust?

08 Jul 2021
July 8, 2021
Password Statistics: What Are Passwords Costing You?
You might think passwords are free but it comes with hidden costs. Here we gathered research data that puts a dollar amount to the true cost of passwords.
21 Jun 2021
June 21, 2021
How Beyond Identity Addresses the Executive Order on Improving Cybersecurity
The Executive Order aims to ensure that the “prevention, detection, assessment, and remediation of cyber incidents is a top priority and essential to national and economic security.”

11 Jun 2021
June 11, 2021
Password Sharing at Work: Exploring Employees’ Habits Around Passwords in the Workplace
Password sharing is common. While it may allow for easier collaboration, there are other noteworthy consequences of passwords floating around the office.
10 Jun 2021
June 10, 2021
What is Device Trust?
Device trust has fundamentally changed, and managing the risks of unmanaged devices is becoming more prevalent and important.

03 Jun 2021
June 3, 2021
A Better Way to Prevent Account Takeover and Other Password-Based Attacks
Account takeover is no joke. In the last year alone, ATO fraud rates have skyrocketed 282%, and in 2017, ATO fraud losses accounted for $3.3 billion. Even worse, the reputation of your organization or individuals within it can suffer greatly from ATO.
![BYOD: Exploring the Evolution of Work Device Practices in a New Remote-Forward Era [Survey]](https://cdn.prod.website-files.com/6835da5ccf38540935c3c9c1/6890d542a2c26923a152372e_65e740febc254d58c4a0188b_bring-your-own-device.webp)
28 May 2021
May 28, 2021
BYOD: Exploring the Evolution of Work Device Practices in a New Remote-Forward Era [Survey]
Bring your own device (BYOD) is becoming an increasingly popular work practice, but there are consequences that haven't always been considered.
14 May 2021
May 14, 2021
5 Key Takeaways from the 2021 Verizon Data Breach Investigations Report (DBIR)
Learn what's the key information you need from the 2021 Verizon Data Breach Investigations Report.

