The Beyond Blog
.png)
15 Sep 2025
Universal Identity Defense for Legacy and On-Prem Applications with Beyond Identity and CrowdStrike
Extend phishing-resistant MFA to Kerberos, NTLM, LDAP, SMB with Beyond Identity + CrowdStrike.

20 Jan 2022
January 20, 2022
Fintech Security Concerns: Solve Them with Stronger and Frictionless Authentication
Learn about the security challenges the fintech industry faces and why stronger authentication stops cyberattacks before they even begin.

11 Jan 2022
January 11, 2022
Announcing Beyond Identity’s New Integration with the Curity Identity Server
Curity integrates with Beyond Identity to deliver non-phishable, passwordless MFA for customer-facing applications.
10 Jan 2022
January 10, 2022
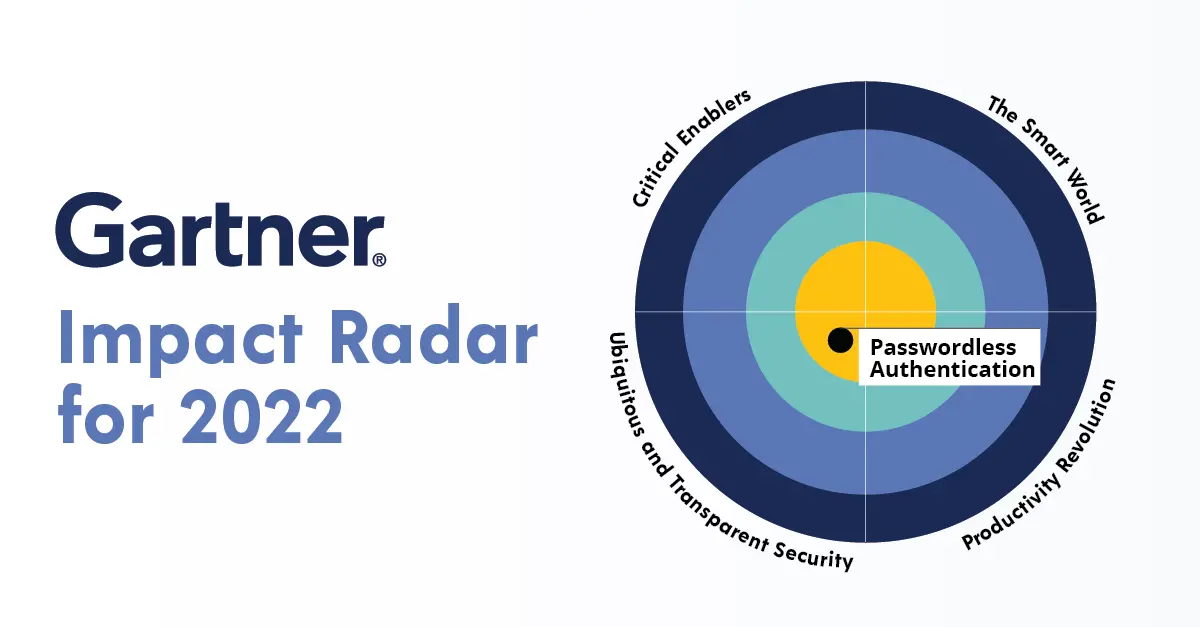
Gartner Designates Passwordless Authentication a Priority for 2022
Gartner has designated passwordless authentication as a key technology that organizations should adopt as soon as possible.

06 Jan 2022
January 6, 2022
What Is Invisible MFA and Why Do You Need It?
Invisible MFA is a new authentication category that breaks the mold of legacy MFA products that are reliant on passwords and other phishable factors.

03 Jan 2022
January 3, 2022
Level Up Microsoft Conditional Access with Beyond Identity’s Device Security Checks
Our integration with Azure AD SSO and other SSOs authenticates users with the strongest and most reliable factors and checks the security of every device.

03 Jan 2022
January 3, 2022
Code Injection Attack: What It Is and How to Prevent It
Code injections pose a significant threat to enterprise cybersecurity. Protecting against code injection attacks is essential for organizations.
30 Dec 2021
December 30, 2021
Secure SDLC Best Practices
Developers can secure the SDLC and reduce the number of vulnerabilities that reach production. Here are four best practices to follow to secure the SDLC.

22 Dec 2021
December 22, 2021
Passwordless MFA vs One-Time Codes
Not all MFA is created equal, but the ones widely used are not the best for customers. Learn the difference between one-time codes and passwordless MFA.

21 Dec 2021
December 21, 2021
Announcing MISA Partnership and Microsoft Azure AD SSO Integration
We’re excited to announce that we’ve joined the Microsoft Intelligent Security Association and we’ve launched an integration with Microsoft Azure AD SSO!

