Resource Library
Explore our collection of resources covering the latest in cybersecurity, industry trends, and expert insights
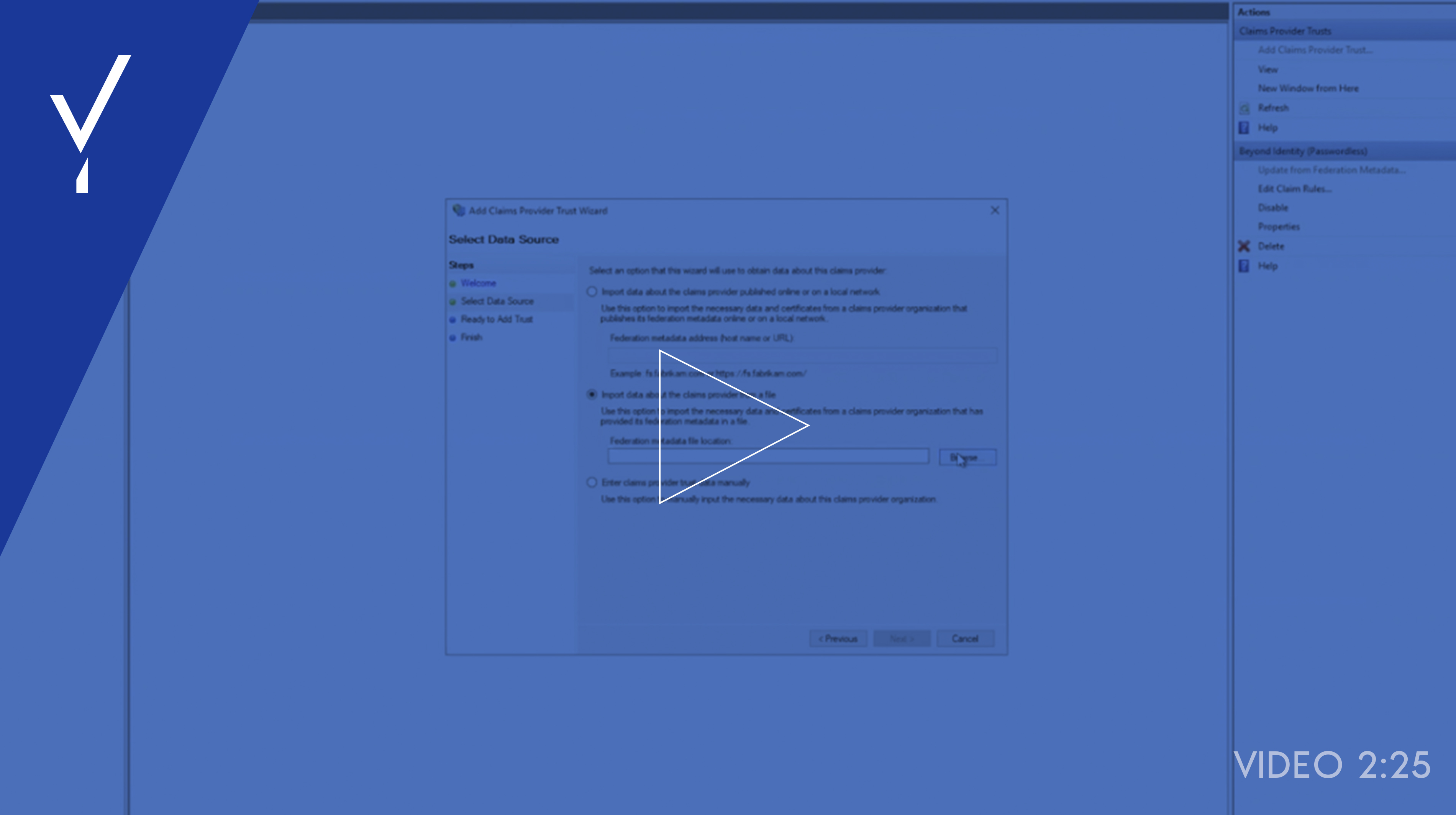
Beyond Identity + Microsoft ADFS Integration
See how to integrate Beyond Identity into your Microsoft ADFS environment.
Authentication Flows Explained
Video 2: Beyond Identity CTO Jasson Casey looks at the backstory of how authentication and access work today

Authentication Meets Zero Trust
Dr. Chase Cunningham, known as Dr. Zero Trust, reviews zero trust and why the rise of Zero Trust Authentication is inevitable.
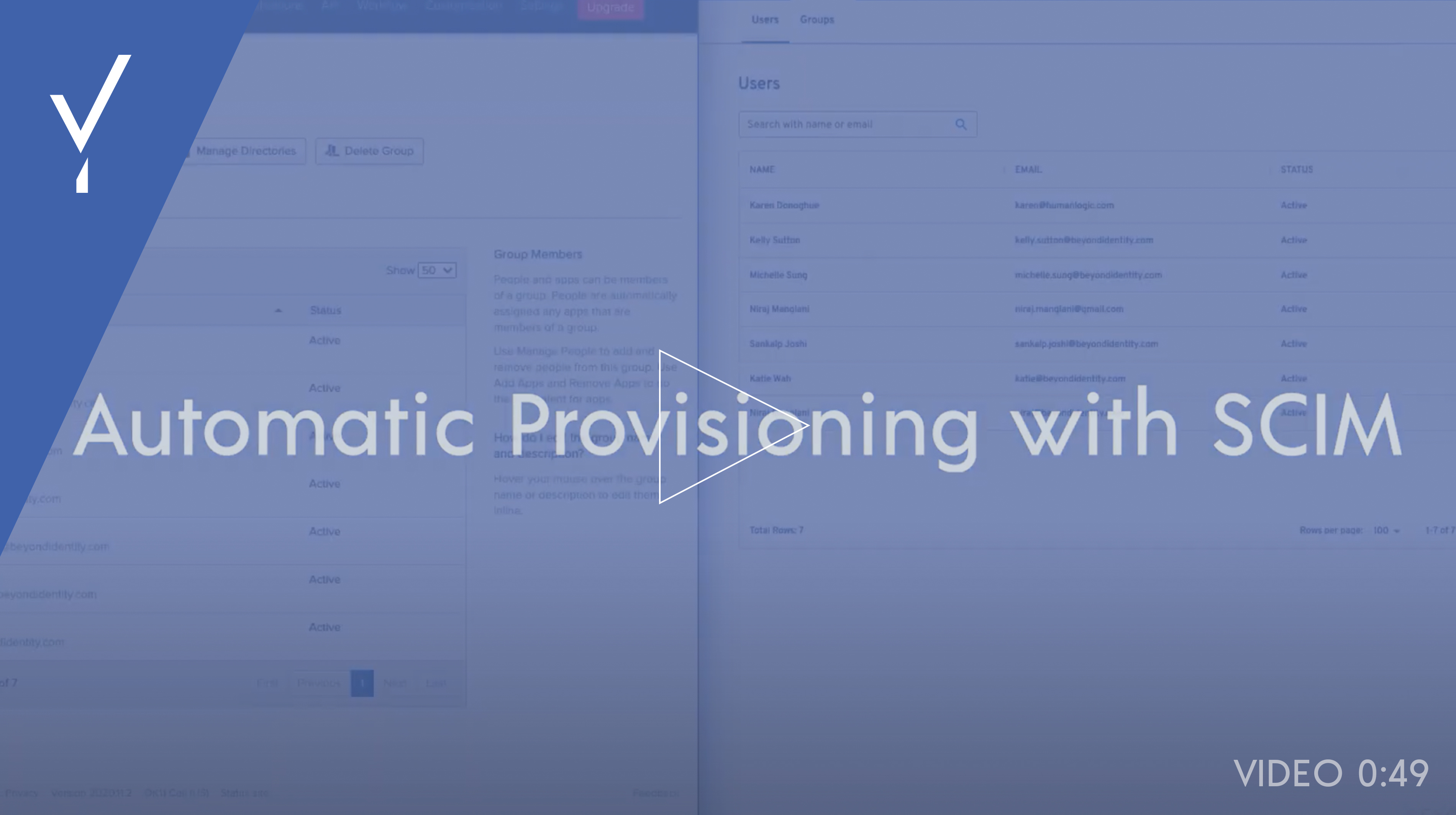
Automatic provisioning with SCIM
Automatically sync users from your mastered directory to Beyond Identity’s directory for easy user lifecycle management.

August Product Update Livestream
See and explore the latest insights on Beyond Identity's new product features, enhancements, and upcoming releases.

Augments Authentication Flows
Video 3: Beyond Identity CTO Jasson Casey drills in and adds more sophistication to the authentication sequence
Asymmetric Cryptography and Secure Enclaves
Video 7: CTO Jasson Casey looks at asymmetric cryptography and secure enclaves and the role they play in zero trust security.

Advance Zero Trust Security
By coupling Beyond Identity's risk-based MFA with Zscaler’s Zero Trust Exchange platform, organizations can achieve high confidence in their users.

