Resource Library
Explore our collection of resources covering the latest in cybersecurity, industry trends, and expert insights

Cybersecurity Mythbusters: Does MFA Stop Credential Theft?
For this episode, we dive into whether or not MFA is the best way to stop credential theft.

CrowdStrike Solution Brief
Combine Beyond Identity and CrowdStrike Falcon to enable zero trust with continuous, risk-based access

CrowdStrike and Beyond Identity
Technical Director Chris Meidinger shows how CrowdStrike's Falcon platform integrates with Beyond Identity’s Zero Trust Policy Engine.

Continuous Authentication and CrowdStrike
The Beyond Identity and Crowdstrike integration allows you to customize security and compliance requirements to secure your resources.
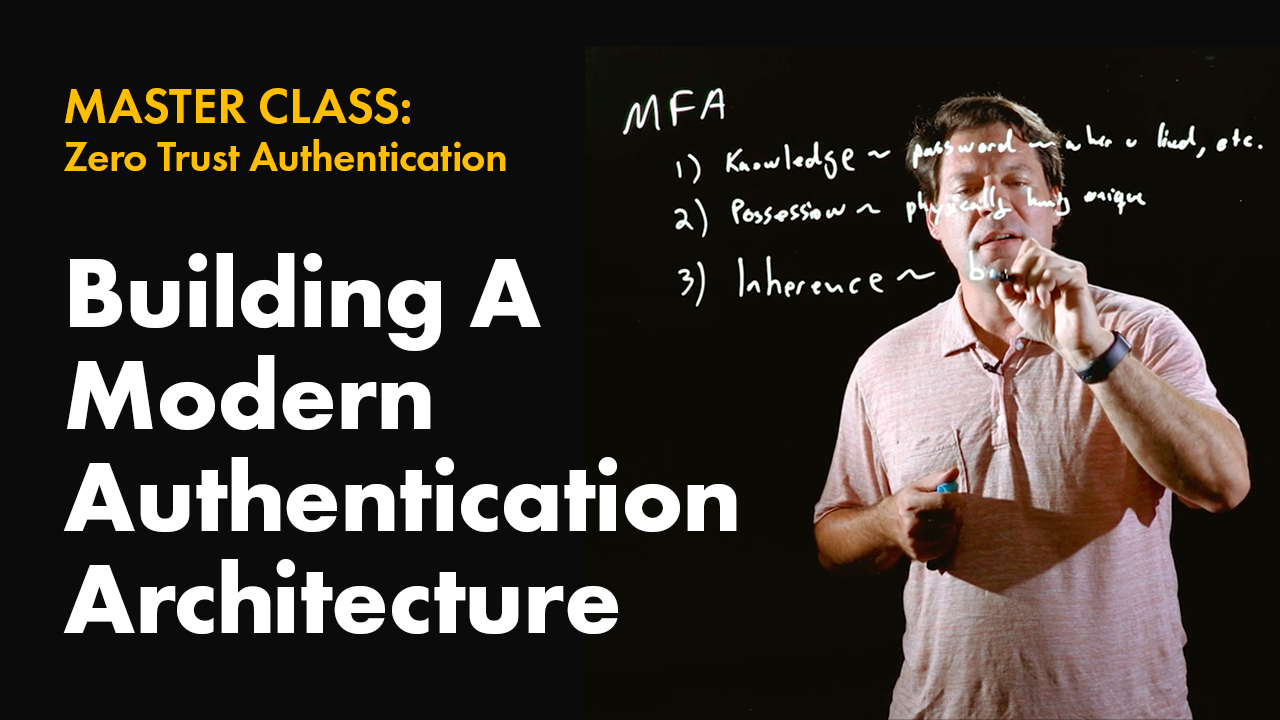
Building A Modern Authentication Architecture
Video 8: CTO Jasson Casey talks about how to actually build up an authentication architecture in an access architecture.
BeyondTrust and Beyond Identity: Secure Remote Access
Deploying Beyond Identity with BeyondTrust will allow your organization to implement a zero trust architecture.

BeyondTrust Solution Brief
BeyondTrust and Beyond Identity have teamed up to deliver integrations that advance zero trust for the most sensitive accounts at every enterprise.

BeyondTrust and Beyond Identity
BeyondTrust technologists review how their privileged access management combines with Beyond Identity's Zero Trust Authentication.

