Resource Library
Explore our collection of resources covering the latest in cybersecurity, industry trends, and expert insights

14 Mar 2023
March 14, 2023
Offensive AI Could Replace Red Teams
This Cybersecurity Hot Takes episode discusses offensive AI and looks at whether AI could eventually replace Red Teams.
.webp)
13 Mar 2023
March 13, 2023
Securing User and Device Access for a Distributed, Multi-Cloud World
Download the definitive book on Zero Trust Authentication to learn how to power zero trust across your enterprise.
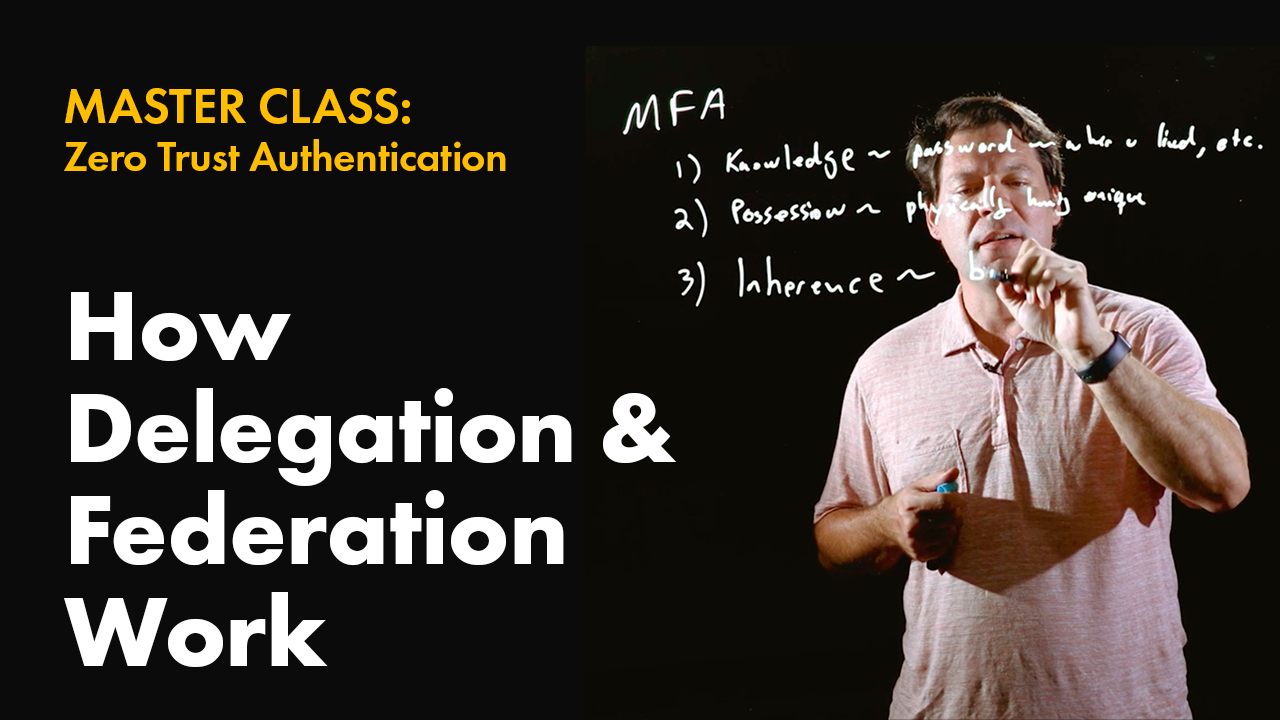
10 Mar 2023
March 10, 2023
How Delegation & Federation Work
Video 4 of the Zero Trust Authentication Master Class series: CTO Jasson Casey takes a deeper look at how delegation and federation work.

07 Mar 2023
March 7, 2023
Identity in Organizations is Too Entrenched to Warrant a Rethink
This Cybersecurity Hot Takes episode discusses identity in organizations with special guest Eric Olden, CEO of Strata.

03 Mar 2023
March 3, 2023
Zero Trust Authentication Defined
Our CTO Jasson Casey shows how Beyond Identity delivers advanced zero trust authentication to serve your extended workforce, developers, and customers.

03 Mar 2023
March 3, 2023
Which MFA is Better: Beyond Identity vs Duo
See a match-up of Beyond Identity's passwordless, phishing-resistant MFA against Duo's phishable and easily bypassed MFA.

02 Mar 2023
March 2, 2023
How Device Trust is Key to Securing Cloud Access
Determining which devices should be trusted is a unique decision made by each organization depending on their risk tolerance and compliance.

01 Mar 2023
March 1, 2023
The Journey to Zero Trust Starts with Authentication
In this episode, the group discusses zero trust, the important role of authentication, and they throw in a little history to keep it interesting.

